When it comes to small businesses, Cyber Security is meant to be too complex to start being repaired or used as marketing jargon in an attempt to make you buy a single product thinking it protects everything you need. Hopefully, this can help you understand what may or may not be necessary to keep your business safe.
Step 1 – Backups
Things are going to go wrong. Before you do anything else, make sure you make backups. Always remember to validate your backups. If you can’t recover your files, backups are just providing a false sense of security. Our recommendation is to have three types of backups.
The first to be configured is a cloud-based version control backup. This can be as cheap as signing up for a $60USD Backblaze account per year for each of your computers. Long-term backups to your data can vary greatly. If you have a small database, it’s not absurd to pay tens of dollars a month for long-term storage with a service like BackBlaze B2.
The second type of backup is a local copy. Any computer-wide image backup and USB drive can help you do everything quickly, even if your entire network is down. If you have malware on your network, some ISPs will block your Internet, so a local backup is always a good idea. Home users can even use Easeus Todo Free as a free option.
The third item to have for backups is a local Data Only copy. This means having secondary storage even if it’s a USB Flash Drive and creating backups from within your software programs to an offline location. If you are using Quickbooks Desktop, for example, having a local backup file gives you the option to just take your data to a clean and working PC. If you keep a cloud-based copy of your data-only backup you can use the exact same procedure for both copies.
Step 2 – Firewall rather than just a router
Typically a business will sign up for the Internet, get a an all in one device, and consider it done. The problem with this is that your internet provider gives you a router, not a firewall. That means there is virtually no protection for your network where you connect to the rest of the world.
Unifi Security Gateway (USG)
Basic (Option #1) Basic cybersecurity has to include keeping bad things out of your network. A router just blindly passes traffic. A simple Firewall provides a core layer of defence with Intrusion Detection and Prevention Systems. IDS/IPS works by looking for known malicious patterns in network traffic and shutting off the bad communications. Installing a Ubiquiti Unifi USG Ubiquiti Unifi USG can give you a very simple interface that almost anyone can use, and add this critical level of security to your network. The Unifi option also gives options for easy to manage Network Switches, and Wireless Access Points to help further improve your network security.
pfSense Firewall Appliance
Basic to Advanced (Option #2) To step up the level of security in your firewall without breaking the bank is to step up to an open-source firewall. There are a lot of commercial firewalls out there, but we’ve found the pfSense option outperforms many firewalls that cost thousands, or even tens of thousands. In use by many seasoned IT Security professionals in deployments as small as homes, and as large as companies doing tens of millions a year in business, or more. This is nowhere as near plug-and-play as an Unifi USG, but ups the game in both security and non-security features. This includes blocking all known bad IPs (lists are maintained online, and will auto-update hourly), being able to block entire countries from connecting to your network, adding VPNs so you can work remotely from your office, and more.

Step 3 – Endpoint Protection
Don’t feel that one program on your computer is the magic bullet against ransomware or other hacking. Virtually no business operates without modern antivirus software, yet every day we can find stories in the news about new victims. Security is multi-layered, and you want to make sure you have the best layers you can. Endpoint protection goes beyond a simple antivirus. Good protection means covering a few basic areas. While anti-virus and anti-malware is a part, so are a local firewall, device control, and reporting. Ideally, any current endpoint protection you consider should have the ability to “sandbox” unknown programs so that if new malware does get to your system, it doesn’t run rampant and do harm before you realize.
With the explosion of ransomware in the news, most Antivirus vendors have labelled their software Endpoint Protection, and have added the required components. Check the software you have to validate it’s not the old style of simple antivirus. It is good to go beyond the antivirus software built-in Windows. Webroot, ESET, Kaspersky and Symantec are among some of the better-known Endpoint programs you may want to consider if you’re just relying on Windows Defender.

Step 4 – Patch Management
With hacking taking place on a scale almost beyond comprehension, most software providers realize that they have to constantly patch their software to not be vulnerable to attack. If you’re not patching the programs on your computer, you’re leaving open doors that you could be closing, and increasing your risk unnecessarily.
Chocolatey – Manage third part patches manually, from each PC. This is a free program that will watch many programs to see if you are missing updates or patches. There are paid alternatives, but installing Chocolatey and the Chocolatey GUI for it can give a huge increase in the level of patching you have with a zero dollar cost. Just open the program, see which programs are out of date, then click to update them. This program doesn’t update Windows, so always have Automatic Updates set up in Windows before you use this.
ManageEngine Patch Manager Plus – This paid program is free for up to 20 Computers and 5 Servers. For a small company, it can provide patch management across multiple computers from a single source. If all of your computers are in one location, can talk to each other through being on a domain, or other means, then this is the better option to go with. Automated deployment of patches for both Microsoft and Third Party applications. Manage Engine Desktop Central is part of a much larger suite of network and system management products, to they give this one away for free in hopes you’ll stay with their platform as they grow.

Step 5 – User Training
Very often even with all of the above steps taken, people still get hit with ransomware or other disruptive attacks that can be avoided. Social engineering is used in targeted hacking to find the easiest way to bypass security; asking the user to do the unknowingly let them in for the hacking.
Two Factor Authentication & Password Managers
One of the first things that will allow people into your accounts is an insecure password. Sites like have I been pwned can give you a good indication of how many places your email and password combination have been exposed. Google Authenticator is free on almost any phone and will let you enable token-based 2FA (Two Factor Authentication) on a huge number of cloud services. Services such as DUO allow you to have all the features of Google Authenticator and add in things like simple Green check / Red X touch authentication from your phone for many websites, services, and even logging in to your computer.
Password managers such as 1Password can suggest very complex, hard to crack passwords for every site you use. IT can automatically enter your passwords on your phone and computer so you’re not typing complex passwords, making it easier to have super secure passwords than to use simple passwords. It can let you know of all the places you’re using the same password, so you can make them all unique. This stops one site you are on that is compromised automatically giving the hacker access to your accounts on other sites you use. It checks your passwords and sites against known breached sites so you can change passwords to secure your accounts. If you don’t like 1Password, there are many other options out there, both free and paid.
Security Awareness Training
Making security front of mind is one of the best ways to protect your business. Training should start with the things that are most common, and cover the areas that would most likely expose your company to risk. Complexities with creating your own awareness training and the low cost of outsourced training from companies such as KnowBe4 and Webroot generally make this an easy item to cross off the list.
Step 6 – Data Leak Protection – If you have client data in your network.
This step is more a simple step if you have IT resources to call upon. This is why it’s last on the list. But it is an important issue. If you keep customer data, PIPEDA requires you to report data loss to the people whose data has been lost. The problem is, most people can’t do this. At the risk of $1,000 per record per unreported breach, it’s not a step that should be overlooked.
DLP software takes some time to set up because you have to tell the system where your customer data is. It also requires setting up rules for normal and abnormal behaviour. If you’re an accountant, accessing 5 customer records an hour is likely normal operations. Accesses 100 records an hour raises alarms and is blocked and reported. If someone accesses data they shouldn’t or accesses too much data, the DLP can report and block the access. The way DLP can do that is by knowing what is confidential, and the rules around what is normal use.
Even though monthly costs of DLP can be as low as about $20 per month per machine with Teramind On-Premise, Initial setup time can be extensive. The more places you have data, and the more rules you need in place, the more complex the deployment job is. It’s always a good idea if you want to deploy DLP to start by reviewing what data you have, where you have it, and what you can eliminate before starting the project. Performing housekeeping on your data before starting can make the difference between an affordable implementation and a horribly expensive implementation.
NMS and SIEM – Going beyond the basics to comprehensive security
Some components of Cyber Security are less plug-and-play. If security is something you want to make a larger part of your business model, we can help by adding Network Monitoring Systems (NMS) and System Incident and Event Monitoring (SIEM) to track and detect more advanced security breaches in real-time. This can be combined with a subscription service for our Security Operation Center to have your systems constantly monitored by our security analysts for the highest level of threat detection. Our services can also include remediation if you don’t have a dedicated IT team so that any issues on your network are not only detected and avoided but also repaired. Repairs can include not only fixes for known updates and process changes after vulnerabilities have been found but even recovery in the event of a breach happening in your company.
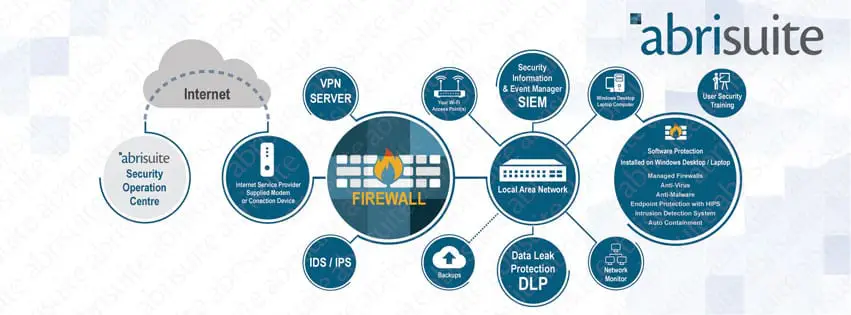
If you want to do this yourself, there should be enough links for you to proceed without problems. Of course, you can always contact Abrisuite to do this for you. Or, if you prefer, have your cybersecurity managed so you don’t have to worry about it.
