The Microsoft Security Intelligence group in their tweet account has published a series of tweets regarding this new malware attacks using Excel documents that are loaded with a malicious macro. Microsoft explain that the ongoing phishing campaign is using HTML redirectors that download the macro-laden MS Excel document that drops the payload. It is interesting that they also use an IP traceback service to track the IP addresses of machines that has been compromised by their malware. This is the first time that this group is using this technique with this purpose.
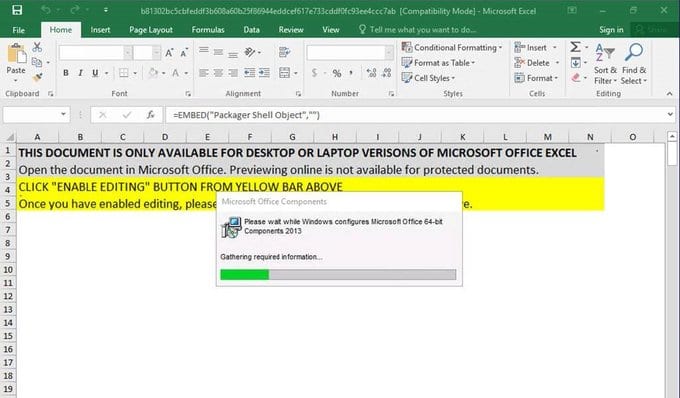
This Evil Corp group is being known since at least the third quarter in 2014 for their attacks on the retail companies and financial institutions using spam attacks that were leveraged by the Necurs botnet.
This group is also known as Dudear, SectorJ04, TA505 and Evil Corp was using this attack in one of the biggest malware campaigns earlier this week. They change some of the tactics used in the past, they are after the data and information of the targets using the Trojan GraceWire.
Microsoft Defender ATP provides comprehensive protection against Dudear, the software detects and blocks the malicious HTML and Excel file and payload. Office 365 by itself is capable to detects malicious attachments and URLs used in emails.
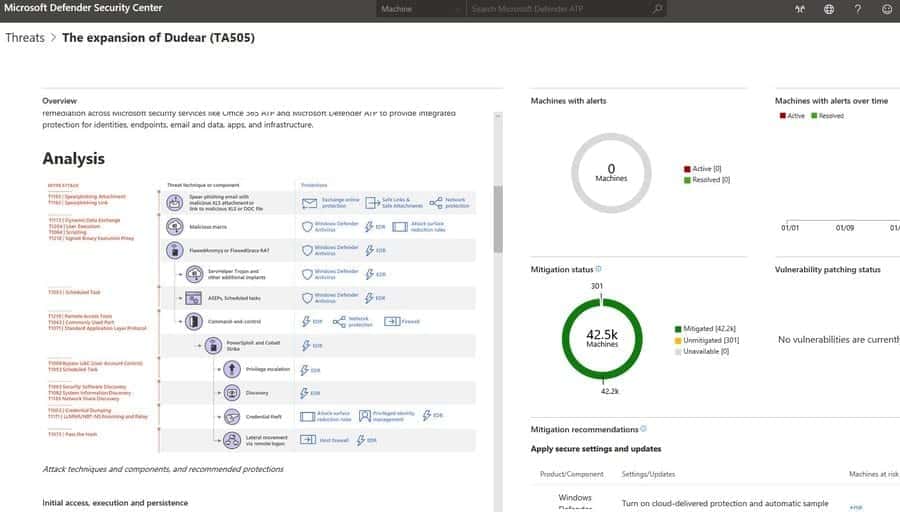
The Microsoft Defender ATP research team has released a Treat Analytics report that customers read to learn more about this threat. Detailing there the techniques and tools used by the Evil Corp. There is also some recommendations in the report about the threat.